About cryptology and AES Professional
Encryption means ciphering data using a key to make the data unusable to others. Decrypting ciphered data deciphers the so called cipher text using a key to reproduce the original data. Encryption is not the same as encoding data, because encoding data solely relies on the transformation algorithm. In contrast, encryption relies on the key and the algorithm. If encoding is used to veil data, the transformation algorithm merely is the key to de-/cipher the data. This not only is very impractical because it would be required to invent a new algorithm each time a new key is required, but cannot be considered as secure, too. There is always a way to reengeneer the algorithm. Using encryption, the algorithm can be publicly available, because the level of security solely depends on the key.
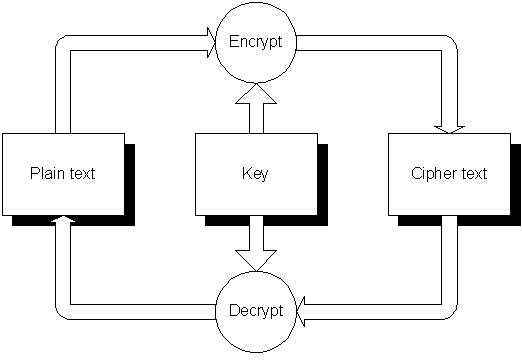
AES, or Advanced Encryption Standard, is the successor of the Data Encryption Standard (DES). AES is a block code with possible key lengths of 128, 192 or 256 bit. The block length can vary between 16, 20, 24, 28 byte and 32 byte. Xbase++ currently works with a fixed block length of 16 byte. AES is considered to be thousands of times more secure than DES because the number of possible keys is higher.
For details about AES, please refer to the AES documentation published by NIST, standard code FIPS-197. See the home page of AES: http://csrc.nist.gov/encryption/aes/
Copyright notes
The AES implementation used by Xbase++ is copyright by Dr. Brian Gladman. Original copyright follows.
Copyright note:
-------------------------------------------------------------------------
Copyright (c) 2001, Dr Brian Gladman <brg@gladman.uk.net>, Worcester, UK.
All rights reserved.
TERMS
Redistribution and use in source and binary forms, with or without
modification, are permitted subject to the following conditions:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. The copyright holder's name must not be used to endorse or promote
any products derived from this software without his specific prior
written permission.
This software is provided 'as is' with no express or implied warranties
of correctness or fitness for purpose.
-------------------------------------------------------------------------
Issue Date: 21/01/2002
The Secure Hash Algorithms, SHA-256, SHA-384 and SHA-512 used by Xbase++ is copyright by Mr. A.D. Gifford. Original copyright follows.
/*
* FILE: sha2.c
* AUTHOR: Aaron D. Gifford <me@aarongifford.com>
*
* Copyright (c) 2000-2001, Aaron D. Gifford
* All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. Neither the name of the copyright holder nor the names of contributors
* may be used to endorse or promote products derived from this software
* without specific prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE AUTHOR AND CONTRIBUTOR(S) ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTOR(S) BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
*/
If you see anything in the documentation that is not correct, does not match your experience with the particular feature or requires further clarification, please use this form to report a documentation issue.